Acknowledgment
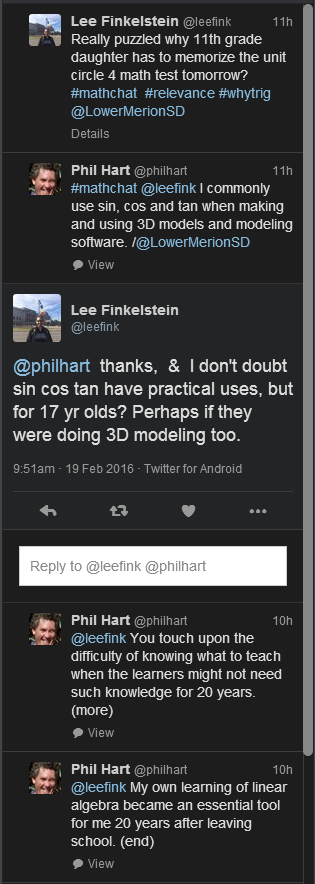
The inspiration for this comes from Lina Zampichelli (Twitter: @micky_lina) with her post in the FS Teach Facebook group. (It is a closed group, so no link, sorry.) It links to an article in Canada’s National Post headlined “Math wars: Rote memorization plays crucial role in teaching students how to solve complex calculations, study says“.
I have been conscious of the recent shift towards “exploration learning” of mathematics, and I have felt uneasy about it, which unease I put down to a sense of nostalgia. Reading that article has made me re-appraise my unease, and the time has come for me to put my own viewpoint about how mathematics might be effectively taught so that it can be effectively learned.
I expect that I might upset a few of today’s younger teachers.
My Use of Mathematics as an Adult
Before describing my own experiences of learning mathematics, it might be useful for me state how I use mathematics in daily life. I do so as a matter of routine, and it is for on a par with reading, writing, speaking and listening: I could not function effectively without my skills in mathematics.
I use my estimation skills when shopping. I do so to check the reasonableness of the total payable. People “behind the counter” sometimes make mistakes, and I will discuss this when I think that I am being overcharged or undercharged. The estimation skill also applies when planning a major expense: what are approximate balances on the credit cards and bank account, what roughly is our monthly income, and what is the cost of the proposed expense. I can then make a yes/no/defer decision.
Basic counting along with addition and subtraction skills can be a time-saver, particularly in shops. At shops where I am known, rather than having to scan six or more items with the same bar code, or wait for the shop assistant to count them, I simply tell them the number, this saving time for both parties. When it comes to presenting cash, I often find that it is quicker and simpler to present money with the cents and low dollars value to the amount where I can receive a single bank note in return. Presenting $20.70 for a total of $10.70 means that I have less metal weighing down my wallet, and the giving of change is also quicker. (It also often brings a smile to the cashier, some of whom seem chronically short of change.)
When it comes to photography, the numbers associated with shutter speed, aperture and focal length always come into consideration when I compose a shot. Here we have gone away from simple counting, and moved into the areas of multiplication, division, and geometry.
Stepping up another gear, a grasp of statistics means that I am able to move from “average care” given by my local doctor, to “better care” with my doctor’s support. Whenever I consult him, I turn up with a printout of all the relevant data presented in statistical form, which allows him to make much better informed decisions. It also allows me to adjust my own medication very rapidly to respond to changes in my own body. A bout of influenza had a very strong impact on some of my vital signs, and ceasing one of my medications for the duration made my life a lot more survivable.
Raising the ante yet again, I use something called “vector matrix algebra” to solve problems with real-world impact. There is a bank of mains power outlets on the island bench in our kitchen. That bank looks a bit like a toblerone chocolate. The quickest and most effective way to find out which angles I needed to use to cut the pieces of wood was by using vectors. Anybody who writes software to display three-dimensional objects effectively on a computer screen needs a thorough understanding of vectors and matrices.
Pulling Out the Bones
In the examples above, as well as in other scenarios, I use the following skills as easily and as unconsciously as I read and write:
- Counting
- Addition and subtraction
- Fractions in all their various forms: a/b, percentage, 12.3456
- Multiplication, division
- Geometry, both Euclidean and spherical
- Trigonometry
- Time, whether measured in femtoseconds or billions of years
- Logarithms and exponentiation
- Algebra and power series
- Equations
- Imaginary numbers
- Base 2 (binary) and base 16 (hexadecimal) numerals
- Statistical presentation and testing for statistical significance
- Vectors matrix algebra
- Calculus
At the bottom of all this lies my ability to count (1, 2, 3, …) which I was taught at a very young age. It was at about this time that I also noticed that not everything could be measured in whole inches, which lay the basis for my later grasp of fractions. I have a very clear memory of learning how to add double and triple digit numbers. Later came the rote learning of times tables, and I am very grateful for having been taught them. Procedures for long multiplication and long division soon followed, whence the concept of a remainder built on my observation of fractions of an inch. I was introduced to simple geometry at about the same time, this built on the concepts of space and measurement. At high school, these ideas were generalised into algebra, which itself served as a basis for learning calculus and the real-world applications thereof. Algebra was also used as the basis for learning vector matrix algebra, as was statistics.
What we have here is a structure of learning that was built on a foundation of a few simple concepts (counting, space, time, and observation) that my teachers helped me to assemble.
Putting this into a historical perspective, I have been the beneficiary of mathematicians whose efforts go back to the ancient Egyptians. The Arabs are credited with the idea of zero as a digit, but this is predated by its appearance in India in about the fifth century CE. Isaac Newton and Gottfried Leibniz are jointly credited with inventing calculus. More recently, vectors came about as the result of about a dozen people over 200 years. Let me put it another way:
If it had not been for the efforts of such people, I would still be counting by using pebbles on the floor of a cave.
Back to the Battlefront
The idea of “discovery-based learning” in mathematics strikes me as being fundamentally flawed. In my view, what is needed is a thorough discussion on what mathematical skills today’s children might want to use in their own adulthoods, and how best to equip them with those skills. Given the developmental benefits described in the article cited at the top of this post, I think it would be madness not to use rote learning to teach times tables.
 and https://www.esafety.gov.au/education-resources/iparent/online-safeguards/parental-controls). While the impact on the users is annoying in both these cases, there is a significant risk that AI failure will have serious impact on other people, including the risk of death.
and https://www.esafety.gov.au/education-resources/iparent/online-safeguards/parental-controls). While the impact on the users is annoying in both these cases, there is a significant risk that AI failure will have serious impact on other people, including the risk of death.